Condensed Study Guide - for CompTIA Security+ Exam Domains
Study Notes for CompTIA Security+
The following are notes that I have compiled from various training sources and from experience in the subject matter. I do not make any claims or guarantees that you will pass by virtue of reading this guide. However, if you are familiar with all this material, it may be a good indication that you are ready for the exam. Additionally, this study guide should also serve as a good refresher and cram tool right before taking the exam.
Ch 1 - Security Basics
- Confidentiality Methods:
- Encryption - the best method
- Access Controls - Identification / Authentication / Authorization (controls access to data)
- Steganography - hides data
- Integrity:
- Hashing - can be used to detect a change in message
- Hashing algorithms, such as MD5, HMAC, or SHA-1, calculate hashes (a number) to verify integrity
- MAC (Message Authentication Code) provides integrity similar to how a hash is used.
- NOTE: There are 3 different meanings to the acronym “MAC” within the context of Security:
- Message Authentication Code (MAC): hashes just mentioned above
- Media Access Control (MAC) addresses: physical addresses assigned to NICs/devices
- Mandatory Access Control (MAC): one of several access control models (see Ch. 2)
- Digital Signatures - provide integrity (as well as Authentication & Non-Repudiation).
- Digital Signatures require the use of certificates (i.e. GPG).
- Availability:
- Increase Availability by adding Fault Tolerance & Redundancies (e.g. RAID, failover clusters, backups, generators, etc.). HVAC systems also increase availability.
- Risk concepts:
- Threat = any circumstance or event with potential to compromise Confidentiality, Integrity, or Availability
- Vulnerability = a weakness (e.g. in hardware, software, configuration, or users operating the system)
- Risk = the possibility or likelihood of a Threat exploiting a Vulnerability resulting in a loss.
- Risk Mitigation = Reducing risk by reducing the chances that a threat will exploit a vulnerability. This is done by implementing controls (also called countermeasures and safeguards)
- Identification / Authentication / Authorization:
- Identification: occurs when a user claims an identity (i.e. with a username or email address)
- Authentication: when user proves the claimed identity (e.g. with password) & credentials are verified
- Access Control systems authorize access to resources based on permissions granted to proven identity
- Combine 2 factors for Dual-Factor Authentication, & 2 or more factors for Multi-Factor Authentication
- The possible AuthN Factors are: (you KNOW, you HAVE, you ARE, and LOCATION or ACTION)
- Something you know, such as a password or PIN (this is the weakest)
- combine Password History with Minimum Password Age to prevent password reuse
- The combination of different characters in a password makes up the key space. Calculate key space with the formula: C^N . C = number of possible characters used, and N = length of the password. For example, a 6-character password using only lowercase letters (26 letters) is calculated as 26 ^ 6 , or about 308 million possibilities. Change this to a 10-character password and the value is 26 ^ 10 , or about 141 trillion possibilities.
- Something you have, such as a smart card or USB token
- Smart Card: provides Confidentiality, Integrity, Authentication, and Non-repudiation.
- Uses embedded certificate and Public Key Infrastructure (PKI)
- Common Access Card (CAC) = specialized type of smart card (token) used by US DoD. Provides capabilities of smart card & also includes picture of user + other readable info
- Personal Identity Verification card (PIV) = specialized smart card used by U.S. federal agencies. Also includes photo ID & provides Confidentiality, Integrity, AuthN & Non-repudiation, like CAC does
- HOTP = HMAC-based One-Time Password, an open standard for one-time pw’s, like those used in tokens & key fobs. A password created with HOTP is valid till it’s used
- TOTP - Time-based One-Time Password, similar to HOTP, but uses a timestamp instead of a counter. TOTP passwords expire after 30 seconds!
- Open standards like HOTP and TOTP are cheaper than proprietary ones.
- Something you are, such as a fingerprint or other biometric identification (Strongest method!!!)
- Two biometric False reading types are:
- False acceptance: when a biometric system incorrectly identifies an unauthorized user as an authorized user. False Accept Rate (FAR, a type 2 error) identifies the % of times false acceptance occurs
- False rejection: when a biometric system incorrectly rejects an authorized user. False Reject Rate (FRR, type 1 error) identifies % of times false rejections occur
- Somewhere you are, such as your location using geolocation technologies, IP address, etc.
- Something you do, such as gestures on a touch screen, handwriting, typing patterns
- IMPORTANT:
- Two or more methods in the same factor of AuthN (e.g. PIN & password) is single-factor AuthN!
- Dual-factor (or two-factor) authentication uses 2 different factors (e.g. a USB token and a PIN)
- Multi-factor authentication uses two or more factors
- Authentication:
- Kerberos: is a Single Sign-On (SSO) authentication implementation
- Provides mutual authentication that can help prevent man-in-the-middle attacks and uses tickets to help prevent replay attacks.
- Kerberos = a network authentication protocol within a Microsoft Active Directory domain or Unix realm. It uses Active Directory and a Key Dist Ctr (KDC) or Ticket Granting (TGT) server to issue timestamped tickets that expire after a time period. It also uses symmetric-key cryptography to prevent unauthorized disclosure & ensures confidentiality
- LDAP: is based on an earlier version of X.500. Windows Active Directory domains and Unix realms use LDAP to identify objects in query strings with codes such as CN = Users and DC = GetCertifiedGetAhead. Secure LDAP encrypts transmissions with SSL or TLS.
- NOTE: LDAP is NOT susceptible to MAC Address spoofing attacks.
- SSO: Single sign-on enhances security by requiring users to use and remember only one set of credentials for authentication. Once signed on using SSO, this one set of credentials is used throughout a user’s entire session. SSO can provide central authentication against a federated database for different operating systems.
- SSO creates a “Transitive Trust” relationship.
- NOTE: Same Sign-On is NOT the same as Single SignOn. In a same sign-on system, users reenter their credentials each time they access another system, but they use same credentials
- IMPORTANT: the primary purpose of SSO is for Identification and AuthN of users. SSO does NOT provide AuthZ! Users claim an identity and prove that identity with credentials.
- SAML (Security Assertion Markup Lang) = XML-based SSO for web apps/browsers
- SAML defines three roles:
- Principal = a User. If necessary, principal requests an identity from identity provider
- Identity Provider = creates, maintains, & manages identity info for principals
- Service Provider = an entity that provides services to principals. For example, a service provider could host one or more web sites accessible through a web-based portal
- Remote Access: RAS (Remote Access Service) provides access to an internal network from an outside source. Clients access a RAS server via either dial-up or a virtual private network (VPN).
- Remote Access AuthN mechanisms:
- PAP - Password Authentication Protocol. PAP sends passwords in cleartext so PAP only as a last resort. PAP authentication uses a password or a PIN. It is susceptible to sniffing attacks. CHAP is more secure than PAP because passwords are not sent over the network in cleartext. Both PAP and CHAP use PPP.
- CHAP - Challenge Handshake Authentication Protocol. Phased out due to MD5!!! CHAP uses a handshake process where the server challenges the client. The client then responds with appropriate authentication information. Only 1 way authN.
- MS-CHAP - Microsoft CHAP=MS implementation of CHAP. Only 1 way authN like CHAP
- MS-CHAPv2 - MS-CHAP is replaced by MS-CHAPv2 which includes several improvements, including the ability to perform (2-way) mutual authentication.
- RADIUS (Remote Authentication Dial-In User Service) provides a centralized method of authentication for multiple remote access servers. RADIUS encrypts the password packets, but not the entire AuthN process. A.K.A. “Network Access Server”
- Diameter is an improvement over RADIUS and it supports EAP (Extensible Authentication Protocol) for security.
- TACACS & XTACACS (Extended Terminal Access Controller Access-Control System) Cisco Systems developed XTACACS as an improvement over plain TACACS.
- TACACS+ (Terminal Access Controller Access-Control System Plus) is a CISCO-released open standard that is an alternative to RADIUS. A benefit of TACACS+ is that it can interact with Kerberos, allowing it to work with a broader range of environments, including Microsoft domains using Kerberos. Additionally, TACACS+ encrypts the entire authentication process, whereas RADIUS encrypts only the password. So TACACS+ includes process-wide encryption for authentication!!! Also, TACACS+ runs on TCP so it has built-in delivery control, and RADIUS runs on UDP so it has to handle that itself.
- Network Policy Server = a Microsoft Server 2012 implementation of a RADIUS server. It helps administrators manage VPNs and wireless networks.
- AAA protocols: provide AuthN, AuthZ, and Accounting (tracking/logging). RADIUS and TACACS+ are both AAA protocols. Kerberos is called AAA but it doesn’t do logging!
Ch 2 - Control Types & Methods
- Control Types: Security controls are classified by NIST Rev 3 as: Technical / Management / Operational. These can be subclassified as Environmental or Physical.
- Technical controls - (aka logical controls) uses/implemented with technology to reduce vulnerabilities
- Ex: Encryption, AntiVirus, IDS, Firewall, Least Privilege (access controls), Biometrics, Routers
- Technical / Physical controls: Mantraps, Video Surveillance, Motion detectors, Proximity readers, Biometrics, Lighting???
- Technical / Environmental controls: Fire suppression systems, EMI shielding, Faraday cage, Hot/Cold aisles, Environmental monitoring, Temperature/Humidity controls
- Management controls - (aka Administrative methods) uses planning & assessment methods to reduce/manage risk. These are procedures implemented to monitor adherence to org security policies
- Ex: Risk Assessments, Planning, Vulnerability Assessments, Pen-Testing, Certification, and annual or regularly scheduled security scans & audits to check compliance with security policies
- Mgmt / Physical controls: Access list, Guards
- Mgmt / Environmental controls:
- Operational controls - help ensure that day-to-day operations of an organization comply with their overall security plan and safeguard all aspects of day-to-day operations, functions, and activities.
- People (NOT technology) implement Operational controls.
- Ex: Awareness training, Config (baselines) & Change Mgmt, Contingency Planning, Media Protection, Physical/Environmental protection, Door Locks and Security Guards at entrances
- Technical / Physical controls: Cameras, Hardware/Door locks, Fencing,Signs, Barricades,
- Technical / Environmental controls: HVAC
- NIST SP 800-53 Rev 3, “Security & Privacy Controls for Federal Info Systems & Organizations” attempts to classify every control as either Tech/Mgmt/Oper, but many qualify as multiple types so Rev 4 eliminates this.
- Control Goals: Another classification of controls is based on their purpose or goal, for ex: Deterrent, Preventive, Detective, Corrective, and Compensating.
- Deterrent controls - attempt to discourage attacks/incidents. You can often describe many deterrent controls as preventive controls. But these are designed to DISSUADE only (i.e.not STOP or eliminate the risk completely)
- Ex: Lighting, Cable locks, Hardware locks, threat of termination
- Preventive controls - attempt to prevent an incident from occurring. Designed to STOP the threat!
- Ex: Hardening, Sec Awareness Training, Security guards, Chg Mgmt, Account Disabling
- Detective controls - attempt to detect incidents after they have occurred. These are PASSIVE.
- Ex: Log monitoring, Trend analysis, Security Audit, Video surveillance (CCTV), Motion detection
- Corrective controls - attempt to reverse the impact of an incident.
- Active IDS, Bkup/Recovery Systems
- Compensating controls - are alternative controls used when a primary control is not feasible/available.
- Temporary use of password/pin until new employee gets a Smart Card
- Cipher locks: require users to enter a code to gain access to an area or room.
- Proximity cards: are credit card-sized access cards. Users pass the card near a proximity card reader and the card reader then reads data on the card. Some access control points use proximity cards with PINs for authentication.
- NOTE: Cipher locks do NOT identify users. Proximity cards can identify and authenticate users when combined with a PIN. Biometrics can also identify and authenticate users.
- Mantraps allow only a single person to pass at a time.
- Sophisticated mantraps can identify and authenticate individuals before allowing access.
- Security guards are physical security controls that can protect access to restricted areas. Security guards can be an effective deterrent to prevent tailgating. They can also check individuals’ identification against a preapproved access list.
- Video surveillance provides reliable proof of a person’s location and activity. It can identify who enters and exits secure areas and can record theft of assets.
- Barricades provide stronger barriers than fences and attempt to deter attackers. Bollards are effective barricades that can block vehicles.
- Maximum password age: defines when users must change their password (password expiration)
- Minimum password age: how long users must wait before changing password again. If you set this to 1 day, it prevents users from changing their passwords until 1 day has passed. This is useful with a Password History to prevent users from changing their password multiple times until they get back to the original password.
- Disable (instead of Deleting) unused accounts, to avoid losing encryption & security keys associated with acct
- Group-based privileges reduce the administrative workload of access management. Administrators put user accounts into groups, and assign privileges to the groups. Users within a group automatically inherit the privileges assigned to the group.
- 4 types of “Logical” Access Controls: Rule-based, Role-based, Discretionary & Mandatory(TS/S/Conf/Pub)
- MAC (SElinux); DAC (Win NT & Linux); Role-BAC (Windows Domains); Rule-BAC (firewalls, routers, IDS/IPS)
- MAC model is the most secure model. Used when access needs to be restricted on Need-to-know basis
- DAC (Discretionary Access) model is significantly more flexible than MAC (Mandatory Access) model
- An inherent flaw associated with the DAC model is the susceptibility to Trojan horses!!!
- The DAC model specifies that every object has an owner, and the owner has full, explicit control of the object. It’s based on the identity of subjects and/or groups to which they belong.
- The MAC model uses sensitivity labels for users and data. Sensitivity labels often reflect classification levels of data and clearances granted to individuals.
- The concept of “Need to know” is similar to the principle of “Least Privilege”, but it only applies to data and data permissions. In contrast, the principle of least privilege applies to permissions and rights. Security-enhanced Linux (SELinux) is one of the few operating systems using the MAC mandatory access control model.
Ch 3 - Network Security
- Lower layers provide services to higher layers.
- Provides an opportunity to define standards at each layer that are independent of the other layers.
- Provides a method to troubleshooting internetworking issues.
- Note that there is not complete de-coupling of layers in TCP/IP!
- Protocols for the OSI layers include:
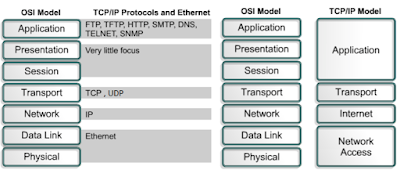
- OSI Layer 7 - Application layer: focuses on user or software application
- OSI Layer 6 - Presentation layer: Formats data. Does encryption, compression, graphics. translates data for application or for transmission, for example encryption
- OSI Layer 5 - Session layer: Tracks bytes to detect end of session. Manages, establish/terminate connections
- OSI Layer 4 - Transport layer: End-to-End Communication. Ensured data integrity, order delivery, flow control. Transfers data between hosts, or includes reliability and error handling
- OSI Layer 3 - Network (Internet) layer: Routing/Translation via Logical IP(v4, v6) addressing. IPSec, ARP, ICMP, IGMP. Transfers datagrams from one node to another
- OSI Layer 2 - Data Link layer: MAC addressing. Ethernet, PPP, 802.11, EAP over NICS, switches, & bridges. Encodes or decodes the data packets and establishes or maintain link between nodes
- OSI Layer 1 - Physical layer: Connectors (i.e. Wireless, UTP Cat6, Optical fibre). Transmits data at the hardware level
- PPP (Point to Point) - to establish a direct connection between 2 nodes, i.e. dial-up
- EAP (Extensible Authentication Protocol) - authentication framework used in Wireless and PPP connections.
- 802.11 - wireless network implementations
- ARP (Address Resolution Protocol) - resolves IP addresses (Network - Layer 3) to MAC #'s (Data Link - Layer 2) but not the other way around.
- ICMP (Internet Control Message Protocol) - these are Pings… Control/Error Messages
- IGMP (Internet Group Management Protocol) - Multicast at IP layer.
- Each layer of OSI model at the source must communicate with its peer layer at the destination!
- During the encapsulation process going down the stack, the protocols at each layer exchange information called Protocol Data Units (PDUs)
- OSI & TCP/IP Similarities:
- Both use layered architecture and are Open in nature
- Both have Application, Transport and Network layers
- Both are packet-switched... not circuit-switched
- OSI & TCP/IP Differences:
- TCP/IP is practical while OSI is not implemented
- TCP/IP combines Physical & Data Link into one layer
- TCP/IP transport layer does not guarantee reliable delivery for UDP (&TCP?)
- OSI LAYER 1 & 2 = "Link Layer" == Physical + Data Link (in OSI) and Network Access (in TCP/IP model) moves data across 1 hop of the network. Physical addresses i.e. MAC (not network addresses) define how devices are addressed at data link layer.
- Link Layer is lowest layer concerned with addressing. Encapsulates packets into frames that are sent via physical layer.
- Link Layer uses CRC (Cyclic Redundancy Check) for Error Control
- Link Layer devices include Switches (and Routers, Hosts)
Layer 1 & Layer 2 Security Slide Notes:
Layer 1: Physical Layer:
- Wired media: TEMPEST = NATO standards to prevent data leakage through electro-magnetic emissions (EMSEC)
- Wireless media: Spread-spectrum modulations may evade detection and jamming.
- Includes Hubs (Layer 1 “legacy” devices). These repeat data and cause collisions
Layer 2: Data Link Layer:
Main functions:
- Addressing: Each device on the LAN has a unique identifier, usually called a hardware or physical address.
- Data framing: Encapsulation of data packets into frames that are sent over the physical layer.
- Hardware includes Layer2 Switches. Use MAC address routing table to know which port to send to. Switches incorporate best features of Hubs and Routers.
- Media Access Control (MAC): Procedures used by devices to control access to the shared transmission medium.
- Error control: To detect errors during the physical layer transmission (e.g. CRC)
Link layer protocols:
- IEEE 802.3/Ethernet | MAC| ARP| NDP | VLANs| Point-to-Point Protocol (PPP) | IEEE 802.11 (a.k.a. WiFi) | EAP
- 6 Key features offered by most network switches are:
Ethernet aspects:
- High performance, widely used,
- Has NO SECURITY (use of VLANs may be used to help overcome this weakness)
- Plug & play for MAC addresses, Backward MAC Address Learning, Spanning Tree Protocol
- The FCS is a Cyclic Redundancy Check(CRC), but it only matters to detect errors at the physical layer.
- Ethernet "Routing" based on Backwards Learning over a Spanning Tree!
- So you start with empty forwarding tables, and there is no need to configure them since they learn on their own.
- All the routing of Ethernet traffic depends on the BPDU… specifically the 16 bits in the Bridge ID!
- NOTE: Backward learning requires a "Loop-Free" topology, otherwise prepare for Broadcast Storms!
- Spanning Tree Protocol (STP) is a safety net for Ethernet to protect against broadcast storms.
VLANs: A physical Ethernet LAN can be split in several Virtual LANs (VLANs)
- The only way to interconnect 2 VLANs is via a Switch with Level 3 capabilities (a.k.a. a “Router”)
- Each VLAN behaves as an independent (logical) LAN:
- Different broadcast domains/IP subnets
- Modern switches also consider the frame VLAN for forwarding it: <Dest. MAC Addr., VLAN> → Output port(s)
- VLANs may employ the same Spanning Tree or different ones:
- Multiple Spanning Tree Protocol (MSTP)
- Frames are assigned to VLANs implicitly (ingress port) or explicitly (VLAN Tag):
- Native port (e.g. user ports): All traffic (standard Ethernet frames) from that port is from the same VLAN.
- Devices that do not support VLAN Tags must be placed in a native port.
- Trunk port (e.g. inter-switch port): Link traversed by different VLANs.
- Ethernet frames are tagged with the VLAN they belong to.
- Trunk ports can also have a native VLAN for untagged frames
Attacks to Ethernet LANs:
- MAC Address Spoofing: Host impersonation. Due to Dynamic Backward Learning, attacker only needs to send 1 frame with spoofed source MAC addr.
COUNTERMEASURE: Statically assign MAC addresses to ports for important MACS (i.e. routers), and less desirable is using Sticky MAC addresses.
- MAC Table Overflow: Data snooping. Hardware MAC address Tables have limited size. Flood a switch with frames containing bogus MAC addresses to overwrite and fill the MAC Table.
COUNTERMEASURE: Limit # of MAC Addresses that can be learnt in a port - but it's a bad idea in an uplink port.
- Spanning Tree Attacks: Data snooping & DoS. To become the Spanning Tree Root you only need to send a BPDU with the lowest priority. It may cause loops (and Broadcast Storms) while the Spanning Tree stabilizes.
COUNTERMEASURES:
- BPDU Guard: Specify which ports can receive STP BPDUs (not from access ports)
- Root Guard: Specify which ports cannot receive the BPDU from the ST Root (not from access bridges)
- LAN Storm: DoS... a single broadcast frame generates many.
COUNTERMEASURES:
- VLANs - Split LAN into separate broadcasting domains
- Storm Control: block broadcast/multicast traffic when some threshold is passed.
- VLAN Hopping Attacks: VLAN intrusion... Double Tagging - if the attacker is in the same native VLAN than the next trunk port, a double tagged frame can cause problems.
COUNTERMEASURES:
- Disable VLAN trunking on access ports
- Reserve a native VLAN just for trunk ports
- Native: If a switch is connected to a Host /PC it is a Native port link.
- Trunk: If connected to another switch , router or VLAN server, it is a Trunk port link.
- You cannot have 2 links working in parallel in Spanning tree protocol!
ARP Vulnerabilities:
- ARP is used to translate IPv4 addresses (OSI layer 3) into Ethernet MAC addresses (OSI layer 2).
- ARP does not authenticate req's or replies, so they can be forged
- a forged req or reply can be used to update the ARP cache of a system with a forged entry (ARP Poisoning), thus redirecting IP traffic elsewhere
- ARP Spoofing attack - causing ARP cache bindings to update to wrong info
- Solution - use Dynamic Arp Inspection (DAI)
Layer 3: Network Layer (IP) Slide Notes:
- Layer 3: Network Layer (in OSI) == Internet Layer (in TCP/IP model) - Provides Logical Addressing... Purpose to send packets from a network node & have them arrive at destination regardless of path taken.
- Network/Internet layer Devices include Routers, Layer3 Switches, and Hosts.
- Routers (being Level 3 devices) use IP addresses to route data as opposed to Switches (Level 2) which use MAC Address
- Provides Connectionless service, with communication between host-to-host using IP address
- IP is a "best effort" service. There may be loss, out of order, duplication, delays in datagram packets.
- Notice it's 5 rows of 4 bytes = 20 bytes
- Header Maximum = 60 bytes (20 bytes TCP + 20 bytes IP + 20 bytes optional)
- Header length includes the "Options" (if any)
- Length represent entire length, including data
- Header checksum is used to make sure the header is not corrupted
- ALERT: Fragmentation usually means that someone is trying to avoid your firewall or IDS detection.
- IP with all binary 0's in host (i.e. 172.10.0.0) is reserved for Network address
- IP with all binary 1's in host (i.e. 172.10.255.255) is reserved for Broadcast address
- ARP (Address Resolution Protocol): It is required because internetworked devices communicate logically using layer three addresses, but the actual transmissions between devices take place using layer two (hardware or MAC) addresses.
IPv6:
- has a 64 bit alignment of packets.
- has a fixed 40 byte header
- eliminates fragmentation! Checksum field is removed
- The way networks operate with mixed-mode IPv4 & IPv6 is via "Tunneling"!
- The IPv6 datagram is carried as payload in an IPv4 datagram (encapsulated) between IPv4 routers
IP Vulnerability:
- Spoofing: End hosts that create IP packets can lie about fields. For example such as the lying about the source by changing source IP address
- Solution - use better authentication method such as IPSec (which encrypts everything from Layer 3 and above)
- Solution - also can use IP Source Guard. IPSG maintains a per-port ACL based on IP-to-MAC-to-Switch port bindings.
- Teardrop Attack: attacker sends 2 IP fragments with overlapping payloads, which cannot be reassembled properly by target host. This causes a crash of victim system due to resource exhaustion.
- Solution - patch the OS
- IP Source Routing (Strict Source Option): can be used for MitM attack
- Doesn't work across Internet as most routers block the Source Route option, but not blocked on internal networks
- NAT: translate public IP to private and vice-versa
- PAT (Port Addr. Translation) - a Static type of NAT that maps 1 single public IP to a private IP
- DNAT (Dynamic Addr. Trans) - uses multiple Public IP addr’s based on load scenario
ICMP Notes Section:
- ICMP (Internet Control Message Protocol) used by hosts & routers to communicate network level info (i.e. error reporting, signaling, pings). They are encapsulated in IP datagrams.
- An ICMP Header max is 40 bytes always.
ICMP Vulnerabilities:
- ICMP has no authentication
- ICMP Source Quench - slows down transmission (Deprecated option)
- ICMP DoS -
- Smurf DoS attack - send a spoofed ICMP Echo Req. to a broadcast address, resulting in every host on target network generating ping replies to victim. This is an Amplification Attack.
- Solution is to reject external packets to broadcast addresses
- ICMP Redirect attack - Redirect msgs should only be sent by routers.
- Ping of Death - attacker sends ICMP echo req. much larger than max IP packet size (65,536 bytes) as fragmented packets. When target reassembles, a buffer overflow causes victim's system to crash.
ICMP Defenses:
- General ICMP defenses include limiting which ICMP types and codes you allow into your network
- Avoid ICMP redirect messages
- Don't allow "unreachable" messages outside your border
DHCP Notes section (NOTE DHCP is a Layer 7 protocol!!!):
- Allow hosts to request IP addresses from a defined pool range.
- Dynamic IP allocation is a 4-step process.
DHCP Attacks:
- DHCP Spoofing attack 1: attacker sends thousands of DHCP req's and exhausts DHCP server's available IP addresses, preventing legitimate servers from getting Addresses.
- Solution - DHCP Rate Limit
- DHCP Spoofing attack 2: where attacker assumes role of DHCP server, giving out false information to other machines, pointing them to the hacker's machine
- Solution - a feature in switches determines which ports can respond to DHCP requests (trusted/untrusted ports)
- Build a MAC-to-IP binding table
Network Layer (IPSec) Slide Notes:
- Why do we need IPsec?
- IP V4 has no authentication
- IP spoofing
- Payload could be changed without detection.
- IP V4 has no confidentiality mechanism
- Eavesdropping
- Denial of service (DoS) attacks
- Cannot hold the attacker accountable due to the lack of authentication.
- IPSec provides Network Layer encryption, plus data authenticity, data integrity, anti-replay protection, non-repudiation, and protection against eavesdropping and sniffing
- IPSec is built into IPv6 (not IPv4). IPv4 can break IPSec when it goes thru NAT (but there is a workaround)
- Identifies key areas for security mechanisms
- • Need to secure the network infrastructure from unauthorized monitoring and control of network traffic
- • Need to secure end-user-to-end-user traffic using authentication and encryption mechanisms
- IPsec provides the capability to secure communications across a LAN, private and public WANs, and the Internet.
- IPSec uses shared secret (symmetric) keys that are distributed via Internet Key Exchange (IKE)
- IPSec has 2 modes: Transport (only payload encrypted) & Tunnel mode (payload and msg header encrypted).
- Use Transport mode on a “Trusted Network”, and Tunnel mode on an “Untrusted Network”
- Principal feature of IPsec is that it can encrypt and/or authenticate all traffic at the IP level (Layer 3 & above), Thus all distributed applications (remote logon, client/server, e-mail, file transfer, Web access) can be secured.
- L2TP (Layer 2 Tunneling Protocol) = IPSec-”like” from Cisco/Microsoft, but NO encryption/confidentiality
- IMPORTANT TIP:
- An “S” for “Secure” at beginning of protocol name implies SSH
- An “S” for “Secure” at end of protocol name implies SSL
- NOTE: add to below port chart that DHCP uses UDP on Ports 67 & 68, and FTP/S uses 989 & 990. For VPN using PPTP open port TCP 1723 (& Protocol ID 47 ???).
- See this link for list of ports
Common attacks:
- Port scanning - finding open ports on hosts listening for traffic. Close ports not in use and block traffic using firewall
- Network Mapping: discovering IP addresses of organization. Block response to ping or all ICMP traffic
- Eavesdropping: countermeasure is to use encryption, i.e. SSH, HTTPS, SFTP IPSec.
- Spoofing/Masquerading: countermeasure is packet filtering via firewall
- Man in the Middle attack: countermeasure is encryption
- Replay attack: countermeasure is to use session keys, nonces, verify timestamps on transmissions, use time-sensitive message digests, etc.
- DoS: examples are SYN flood, Ping of Death, Smurf, UDP Flood. Countermeasures include, block ICMP messages, block broadcast packets at firewall.
Layer 4: Transport Layer
- Firewalls use “Whitelist” principle and usually operate on Layer 4 (Transport), although most firewalls CAN be Layer 3 devices as well (i.e. routers with firewall capability on the edges of your network). They implement Allow/Deny rules to apply Least Privilege and Implicit Deny concepts. They can block nearly all attacks at border (firewall) with following 5 rules:
- Layer 4 Protocols include: TCP and UDP
- TCP
- TCP Header = 20 bytes [+40 bytes]
- Source & Destination ranges from 0 - 65,535
- TCP 3-way handshake (SYN, SYN/ACK, ACK)
- When Server receives SYN, it spawns a thread, allocates memory on its connection queue and begins tracking half-open connection, and waits for ACK from source (often for more than 1 minute). When connection queue fills up, no more connections can be accepted, at this point legitimate clients are denied… This is classic DoS attack! So TCP is Vulnerable to SYN flooding.
- When spoofing, Attackers often spoof using unresponsive (non live) addresses to prevent RST’s from freeing up the target’s (victim) connection queue resources. But interactive traffic only works if attacker is on same LAN as spoofed Address (MiTM)
- Each TCP connection has a State (Seq #, Port #). These are easy to guess. Packets can be injected into connections. “Trusted” machines don’t require Authentication, so Attacker can pretend to be trusted by spoofing IP Addr. But they have to predict initial Seq #.
- Security Issues:
- TCP connection requires/uses state (SYN Flooding [DoS] attack)
- Countermeasures:
- TCP SYN Cookies - with cookie, ensures that responder (server) remains stateless until initiator produces at least 2 messages. Will use the Sequence # field from TCP Header to store the 32 bit cookie value. After initiator responds with ACK, cookie is regenerated by responder and compared with cookie returned by initiator. Cookie contains a Rijndael or crypto hash of Src Addr/Port, Dest Addr/Port, Time, Server Secret. NOTE: if source IP address is bogus, attacker can’t confirm with the return cookie step on.
- Random Queue Deletions - if SYN queue is full delete a random entry. Legitimate connections have a chance to complete and fake ones eventually deleted. Easy to implement
- TCP state easy to guess ( [Blind] TCP Connection spoofing attack) - here attacker first sends TCP connection req’s to Bob to guess seq #, then SYN-Floods Alice to kill that server, then sends SYN’s to Bob spoofing Alice’s server
- Countermeasures:
- Use Random ISNs - a random seq # to make it harder to guess
- DoS by Connection RST - here attacker guesses Seq # and closes it by sending a RST segment.
- Countermeasures:
- Use Random ISNs - a random seq # to make it harder to guess
- UDP
- UDP Header = 8 bytes header length. Connectionless protocol with no flow control, Acknowledgement or msg continuation.
- UDP Attacks:
- UDP Fraggle (Packet Magnification) - Uses UDP echo packets (similarly to ICMP echo packets in Smurf attack). This achieves smaller amplification than Smurf though.
- UDP Ping Pong - Echo uses port 7, and anything it receives it echoes back. And Chargen (random character generator) uses UDP port 19. If both services are enabled, attacker spoofs connections to a hosts Chargen port causing a ping pong to burn bandwidth.
- Countermeasures:
- Use Application-Aware Proxie
- Don’t expose apps/svcs you don’t need (e.g. echo, daytime, chargen)
- In Network (IP) Layer [#3] - use IPSec: protects against hijacking, injection, DoS due to conn RST’s, IP Addr spoofing
- In Transport Layer - use SSL/TLS/DTLS and SSH to protect against hijacking and injected data.
- Use SYN Cookies - to protect against spoofed packets.
- UTM and Web Security Gateways are synonymous devices...
- UTMs are all-in-one security devices. Can be a single-point of failure if not careful!
- URL Filter, Content Inspection, Malware & Spam filter, Router/Switch/Firewall, IDS/IPS
- Web Security Gateways: “nearly identical to UTM devices”, but its real strength is in content filtering
Ch 4 - Securing your Network
Subnet: Split into Network and Node portions (i.e. 255.255.255 = Network/Subnet portion & .0 is Node portion)
So 192.168.2.15/255.255.255.0 == 192.168.2 (as the subnet) and .15 is the node/machine
And 192.168.1.15/255.255.255.0 == is on another subnet, so these two machines CANNOT communicate with each other UNLESS a Router is set up between them!!!
Subnet shorthand: 255.0.0.0 == /8; 255.255.0.0 == /16; 255.255.255.0 == /24 (see this tutorial link)
So the network portion (and subnets associated with the network portion) is defined by the # of bits turned on in octets
RADIUS: How to perform centralized (AAA) Authentication, Authorization, Accounting.
RADIUS is a stateless client-server AuthN/AuthZ/Acctng protocol, runs on UDP. Uses a Shared-Secret, supports user-roaming. The authentication uses a random Nonce.
PPP (Point-to-Point) - a Link Layer protocol provides datagram encapsulation, authentication (via PAP, CHAP, EAP)..
- PAP - Password Auth Prot. (credentials sent in plaintext!)
- CHAP - Challenge Handshake Auth Prot. (user responds with challenge in MD5 - vulnerable to dictionary attacks, but NOT to Replay attacks)
- MS-CHAP2 - dual challenge but can be broken by breaking DES key
- EAP - Extensible Auth Prot. is an AuthN framework that provides guidance for AuthN methods.(can use several AuthN protocols, but requires an encapsulation protocol to wrap it all up in (i.e. RADIUS, Diameter, PEAP)
EAP - know that the initial request to authenticate is sent from the Authenticator to the Supplicant.
The most relevant versions of EAP today are:
- EAP-TLS (Transport Layer Security): One of the MOST secure standards implemented! TLS messages encapsulated in EAP ones (TLS over EAP): Mutual authentication with client certificates
- EAP-TTLS (Tunnelled TLS): Two phases: 1) TLS over EAP authentication with anonymous client identity, 2) Exchange of Attribute-Value Pairs (AVP) over TLS over EAP
- PEAP (Protected EAP): Two phases: 1) TLS over EAP authentication with anonymous client identity, 2) 2nd EAP session (e.g. EAP-MSCHAPV2) tunnelled in TLS over EAP. NOTE: PEAP Mutual Auth prevents Man-in-the-Middle attacks if properly configured!
- LEAP - is a CISCO implementation as extension of EAP, but is replaced by PEAP.
- The most secure EAP method is EAP-TLS, which requires a certificate on the server & on each of the wireless clients. PEAP and EAP-TTLS require a certificate on the server, but not the client. PEAP is often implemented with MS-CHAPv2. LEAP is proprietary to Cisco and does not require a certificate.
Authentication with PEAP - uses a pair of keys for authenticating, then uses another pair of keys for actual tunnel building and transmission.
WiFi Authentication:
- IEEE 802.11 (a/b/g/n) - is the WiFi standard
- 802.1x is Port Security/Network Access Control (NAC) for wireless networks. It’s a std’s & protocols suite by IEEE
- NAC (Network Access Control - basically performs health check on machines connecting to the network to ensure they pass. If not they are forwarded to remediation servers to fix the issues. Once they pass they are allowed to authenticate with the Domain Controller and connect to the system.
- WEP - broken. No Nonces used. Request/Response exchange. Uses a new Initialization Vector (IV) for every packet.
- WEP Weaknesses -
- Though it uses a different IV for each packet, it uses the same set of IVs over and over in a loop, therefore the IV reuse is a major weakness. NOTE: IV sometimes a.k.a a Nonce
- It also has no replay protection or real integrity protection.
- Also WEP uses the first 256 bytes of RC4 (pseudo random nbr gen) which are the vulnerable portion of RC4!
- Uses only one key! Also same key for Encryption as Decryption
- PTS Attack (Pyshkin-Tews-Weinmann) breaks it in 60 seconds
- WPA - attempts to addresses WEP weaknesses.
- Uses Key hierarchy and EAPOL Key
- Uses EAPOL+RADIUS for Authentication
- Each Station shares a different temporary key with the AP
- Also uses Group keys for broadcasting
- Prevents replay attacks
- Uses 4-way handshake
- Avoids IV reuse and uses a different RC4 key for each frame
- WPA Weakness - Uses SHA-1 for key derivation
- WPA2 - solves WPA problems,
- is NOT backwards compatible to WEP as WPA is
- Maintains EAPOL auth & key distribution
- Replaces RC4 cipher with AES (required new hardware to use AES). it technically uses AES-based CCMP
Ch 5 - Securing Hosts & Data
- Hardening a server makes it more secure from its default installation. Disabling unnecessary services and protocols reduces the attack surface of a system and improves its overall security posture.
- Trusted OS - has enhanced security features (esp. AuthN/AuthZ) to restrict data access/usage by people/pgms. Usually uses Mandatory Access Control (MAC)
- Baseline types - There are several different types of baselines, including:
- Security baselines: used to ensure systems start in a secure state
- Configuration baselines: used to ensure systems are deployed consistently . Important to keep this up to date! The differences between a configuration baseline and a security baseline can be a little fuzzy. The security baseline settings are strictly security related. The configuration baseline settings ensure consistent operation of the system. However, because the configuration baseline contributes to improved availability of a system, which is part of the security triad, it also contributes to overall security.
- Host software baselines: used to document/list all software installed on host systems
- Application configuration baselines: used to document appropriate application settings
- Performance baselines: used to identify when system performance is degrading
- Group Policy benefits:
- Can be applied to multiple users easily
- Regularly Re-Applies policy settings, so can undo a compromise/change to settings
- Imaging benefits:
- Secure starting point
- Reduced costs
- U.S. Government Configuration Baseline (USGCB) - these images include settings that are compliant with Security Content Automation Protocol (SCAP). SCAP validation functionality is built in to many vulnerability scanners, allowing them to verify the security settings haven’t been modified.
- Virtualization - When using VMs, you can create them so that they are isolated in a sandbox environment. Sandboxing prevents the VMs from interacting with any other VMs, the physical host, or devices on the network.
- VHD files. These files hold data on the virtual hard disk (VHD) within the VM. For example, if the VM has a C and a D drive, these files contain the contents of the C and D drives.
- XML files. These files contain the configuration details of the VM within Extensible Markup Language (XML) files. Each VM includes an associated XML file and each snapshot includes an associated XML file identifying the configuration at that time.
- AVHD files. These are automatic VHDs, more commonly known as differencing disks. They hold the differences between the current disk and a previously created snapshot.
- VSV files. These files hold the saved state for devices associated with the VM. Instead of shutting down a VM logically, it’s also possible to save the current state and turn it off. This is similar to using Hibernate mode in a laptop. Hibernate mode saves the current state of the laptop in a file and turns the laptop off. When you power it back on, it returns to the exact same state as it was before going into Hibernate mode.
- BIN files. These files hold the memory for systems that are in a saved state.
- Virtual local area networks (VLANs) separate or segment traffic on physical networks. You can also create VLANs using virtual switches within a virtual environment hosted on a physical server
- VM escape is an attack that allows an attacker to access the host system from within the virtual system.
- Patch management procedures ensure that operating systems and applications are up to date with current patches. This protects systems against known vulnerabilities.
- Static Environments:
- SCADA
- Embedded systems - printers, smart TV’s, heating, ventilation, and air conditioning (HVAC) systems.
- Mobile devices
- Mainframes
- Game Consoles
- In-Vehicle computing systems
- Protecting Static Systems:
- Redundancy & diversity controls. Diversity refers to protecting systems with diverse security controls. This is often done by using security controls from different vendors.
- Network Segmentation
- Security Layers - Defense in depth methods
- Application Firewalls
- Manual Updates
- Firmware Version Control
- Wrappers. Some operating systems such as Linux and Unix use Transmission Control Protocol (TCP) wrappers to filter traffic coming in and out of a system.
- Mobile device security includes device encryption to protect the data, screen locks to help prevent unauthorized access, and remote wipe capabilities to delete all data on a lost phone. Radio-frequency identification (RFID) methods are often used for inventory control.
- Mobile device management (MDM) includes the technologies to manage mobile devices such as smartphones and tablets. The goal is to ensure these devices have similar security methods in place as desktop computers. Mobile device management tools help ensure systems are up to date with current patches and have up-to-date antivirus installed. These tools often block devices that are not up to date.
- MDM tools features:
- Patch management. Patch management ensures that mobile devices are kept up to date with current patches. Antivirus management.
- Antivirus management ensures systems have antivirus software installed and it is up to date with current definitions.
- Application control. Some MDM tools can restrict what applications can run on mobile devices. They often use application whitelists to control the applications.
- One of the challenges with file-level encryption is that the encryption can be lost if an authorized user copies encrypted files to another disk that doesn’t support encryption. Solution is to use USBs with whole-device or full-disk encryption.
- Trusted Platform Module (TPM) - is a hardware chip on the computer’s motherboard that stores cryptographic keys used for encryption. Many laptop computers include a TPM, but if the system doesn’t include a TPM, it is not feasible to add one. Once enabled, the TPM provides full disk encryption capabilities. It keeps hard drives locked, or sealed, until the system completes a system verification and authentication process. The TPM ships with a unique Rivest, Shamir, Adleman (RSA) key burned into it, which is used for asymmetric encryption. Additionally, the TPM can generate, store, and protect other keys used for encrypting and decrypting disks. TPMs use three categories of encryption keys:
- Endorsement key. The manufacturer embeds an endorsement key into the TPM. This stays with the TPM throughout its lifetime.
- Storage root key. The TPM creates the storage root key when a user adds a TPM owner password and activates the TPM. The TPM uses this key to create and protect other encryption keys used within applications.
- Application keys. These keys are derived from the storage root key and applications use them to encrypt disks. For example, Microsoft BitLocker uses an application key to encrypt entire disks.
- Hardware Security Module (HSM) is a security device you can add to a system to manage, generate, and securely store cryptographic keys. A hardware security module (HSM) is a removable or external device that can generate, store, and manage RSA keys used in asymmetric encryption. Many server-based applications use an HSM to protect keys.
- Data loss prevention (DLP) techniques examine and inspect data looking for unauthorized data transmissions.
- DLP is a control that forces people to authenticate before giving them rights to take data out/off the network.
- NOTE: IPS vs IDS… an IPS is like an “Active” IDS with one major difference: an IPS is ALWAYS placed in-line with the traffic so it can prevent an attack from reaching the network!
- NIDS cannot detect anomaly on individual workstations, unless anomaly causes network anomalies. Also NIDS cannot decrypt traffic so it can only monitor unencrypted network traffic
- HIDS can detect malware that traditional AntiVirus apps might miss
Ch 6 - Malware and Social Engineering
- Armored viruses use various techniques to make the reverse engineering process more difficult for the AV researchers. Some methods used by armored viruses are:
- Complex code. Some armored viruses use confusing code specifically designed to mask what the virus is actually trying to do.
- Encryption. Some compilers encrypt the code with the virus, making it more difficult to decompile. This code must first be decrypted before it can be decompiled.
- Hiding. Some viruses attempt to hide their actual location by tricking AV software into thinking the file is located somewhere else.
- Some virus developers use polymorphism as a method of armor. Polymorphic malware has the ability to morph or mutate when it replicates itself, or when it executes.
- A worm is self-replicating malware that travels throughout a network without the assistance of a host application or user interaction. Worms consume network bandwidth.
- A logic bomb is a string of code embedded into an application or script that will execute in response to an event.
- Malware such as Trojans often install backdoors on systems to bypass normal authentication
- Another Trojan method that has become popular in recent years is rogueware, also known as scareware. Rogueware masquerades as a free antivirus program.
- Remote Code Execution == “Arbitrary code execution”. These attacks are the result of application vulnerabilities, and can allow complete takeover of victim’s computer or remote execution of commands
- LSO’s - Locally Shared Objects (i.e. Flash Cookies) can track user’s browsing behaviors and can remain on a system even after the user has cleared tracking objects from their browsers
- The computers in a botnet are called zombies and they will do the bidding of whoever controls the botnet.
- In addition to modifying the internal operating system processes, rootkits often modify system files such as the Registry. In some cases, the rootkit modifies system access, such as removing users’ administrative access.
- Rootkits have system-level access to systems. This is sometimes called root-level access, or kernel-level access, indicating that they have the same level of access as the operating system. Rootkits use hooked processes, or hooking techniques, to intercept calls to the operating system. In this context, hooking refers to intercepting system-level function calls, events, or messages. The rootkit installs the hooks into memory and uses them to control the system’s behavior.
- Antivirus software often makes calls to the operating system that could detect malware, but the rootkit prevents the antivirus software from making these calls. This is why antivirus software will sometimes report everything is OK, even if the system is infected with a rootkit. However, antivirus software can often detect the hooked processes by examining the contents of the system’s random access memory (RAM).
- Another method used to detect rootkits is to boot into safe mode, or have the system scanned before it boots, but this isn’t always successful. It’s important to remember that rootkits are very difficult to detect because they can hide so much of their activity. A clean bill of health by a malware scanner may not be valid.
- Spyware monitors a user’s computer. Pop-ups are annoying windows that appear while browsing. Many pop-ups are adware designed to market products to users.
- Spam is unwanted or unsolicited email.
- Phishing is malicious spam… Phishing is the practice of sending email to users with the purpose of tricking them into revealing personal information or clicking on a link. A phishing attack often sends the user to a malicious web site that appears to the user as a legitimate site.
- Spear phishing is a targeted form of phishing. Instead of sending the email out to everyone indiscriminately, a spear phishing attack attempts to target specific groups of users, or even a single user.
- Whaling is a form of spear phishing that attempts to target high-level executives.
- Vishing is a form of phishing that uses the phone system or VoIP. Vishing attacks use the phone system to trick users into giving up personal and financial information. It often uses Voice over IP (VoIP) technology and tries to trick the user similar to other phishing attacks. When the attack uses VoIP, it can spoof caller ID, making it appear as though the call came from a real company.
- Spim is a form of spam using instant messaging (IM).
- Bluetooth attacks:
- BlueJacking - sending unwanted messages to device (mostly harmless)
- BlueSnarfing - access/theft of info from device (i.e. email, contacts) using tools hcitool & obexftp
- BlueBugging - attacker takes over phone (i.e. listen to calls, enable call-forwarding, send msgs, etc.)
Ch 7 - Identifying Advanced Attacks
- DDoS attacks - often include sustained, abnormally high network traffic on the network interface card of the attacked computer.
- Smurf attack - sends ping out as a broadcast. In a broadcast, one computer sends the packet to all other computers in the subnet. The smurf attack spoofs the source IP. If the source IP address isn’t changed, the computer sending out the broadcast ping will get flooded with the ICMP replies. Instead, the smurf attack substitutes the source IP with the IP address of the victim, and the victim gets flooded with these ICMP replies.
- SYN Flood attack - never completes 3-way handshake. Countermeasure=Firewall & IDS Flood Guards
- Christmas Attack - port scan (& DoS attack) that finds details of OS (via flag settings/analysis in TCP packet header). Countermeasure = IDS/IPS
- ARP Poisoning attack - a form of MiTM attack, which misleads computers & switches regarding association of IP to MAC addresses. Countermeasure = Kerberos Authentication
- Replay attacks - Countermeasure = Kerberos (timestamps, and sequence #’s/nonces)
- Brute Force Password attacks - require most computing power. Counter = Lockout policies, complex pw’s
- Birthday (Hash) attack - a password that produces same hash value (Hash Collision). Counter=SHA2
- Dictionary attack - takes advantage of a predefined list of words
- Rainbow tables - precomputed hash values for cracking passwords. Counter= Salting PW, Complex PW
- DNS Poisoning - modify/corrupt DNS results. Counter=DNSSEC
- DNS Pharming - modify/corrupt the hosts file on computer. Counter=Access Controls?
- Typo Squatting - misspelled URLs, a.k.a URL Hijacking attack
- Banner grabbing - gain info about a remote server, often part of a fingerprinting (e.g. use telnet)
- Watering Hole attack - infect commonly visited websites
- Web servers are highly susceptible to several types of attacks, such as buffer overflow attacks and SQL injection attacks, because they commonly accept data from users.
- Buffer overflows occur when an application receives more data than it can handle, or receives unexpected data that exposes system memory. Buffer overflow attacks often include NOP instructions (such as x90) followed by malicious code. When successful, the attack causes the system to execute the malicious code. Input validation helps prevent buffer overflow attacks.
- An integer overflow attack attempts to create a numeric value that is too big for an application to handle. The result is that the application gives inaccurate results.
- Both NoSQL & SQL databases are susceptible to command injection attacks if developers do not implement input validation techniques. SQL databases use SQL queries and are susceptible to SQL injection attacks.
- LDAP injection attacks attempt to access or modify data hosted on directory service servers.
- A transitive access attack attempts to access a back-end server through another server. A SQL injection attack is an example of a transitive access attack that can bypass many other security controls.
- Fuzzing sends random strings of data to applications looking for vulnerabilities. Administrators use fuzz testing to test applications and attackers use fuzzing to detect attack methods.
Ch 8 - Managing Risk
- Vulnerability = a flaw or weakness in software or hardware, for example...
- Lack of updates/patches
- Default Configurations
- Lack of AntiVirus/Malware protection
- Lack of Firewalls
- Lack of Organizational Policies
- Threat = a potential danger that can compromise CIA of a system. The result = a negative impact on the org
- Risk = the likelihood that a threat will exploit a vulnerability.
- Residual Risk = risk remaining after managing risk.
- Impact = the magnitude of harm that can be caused if a threat exercises a vulnerability.
- Threat Vector = (aka an attack vector) refers to the method used to activate the threat and can originate from three primary sources: external (outsiders), internal (insiders), and the supply chain (suppliers).
- Types of Threats:
- Natural Threats - i.e. natural disasters like hurricanes
- Malicious Human Threats
- Accidental Human Threats
- Environmental Threats - e.g. chemical spills, pollution
- Threat Assessments - Org’s use to Identify/Categorize Threats. Predict Threats against a system and Likelihood that a Threat Vector will activate a Threat. Identify potential Impact of threats, and Identify security controls to mitigate threats.
- Risk Management - practice of identifying, monitoring, & limiting risks to a manageable level.
- Avoid Risk - not providing a service or not participating in a particular risky activity (i.e. Backout)
- Accept Risk - When the cost of a control outweighs a risk, an organization will often accept the risk
- Transfer Risk - e.g. to an insurance company
- Mitigate Risk - implement controls to reduce the risk. Ex. install AV and use Firewalls
- Deter Risk - deter risk by implementing a control (e.g. Security Guards & Visible Cameras). CompTIA separates this one from Mitigation of Risk (for some dumb reason).
- Risk Assessment - important task in Risk Management, which begins with identifying assets & values, then ID’s Threats/Vulnerabilities/Likelihood/Impact, etc. It is a Snapshot assessment. Results of a risk assessment are highly protected. Normally, only executive management and security professionals will have access to these reports. Assessments types include…
- Quantitative assessment - use actual numbers (e.g. dollars) of cost & asset values.
- SLE (Single loss expectancy) = the cost of any single loss.
- SLE = V (value of svc or function) x EF% (Exposure Factor)
- ARO (Annual rate of occurrence) = indicates how many times the loss will occur in a year. If the ARO is less than 1, the ARO is represented as a percentage. For example, if you anticipate the occurrence once every two years, the ARO is 50 percent or .5
- ALE (Annual loss expectancy): ALE = SLE × ARO.
- You can reformat the formula. Any of these are valid:
- ALE = SLE × ARO
- ARO = ALE / SLE
- SLE = ALE / ARO
- Qualitative assessment - use judgements, and is based on probability & impact. Surveys may be used. Low/Med/High values are assigned and points are assigned based on those L/M/H assessments.
- Semi-Quantitative analysis method - a middle ground between the two.
- Metrics to Identify Risk:
- Mean time between failures (MTBF). The mean time between failures (MTBF) provides a measure of a system’s reliability and is usually represented in hours. “This is recoverable, whereas MTTF is not!”
- Mean time to failure (MTTF). The mean time to failure (MTTF) is the length of time you can expect a device to remain in operation before it fails (and then has to be discarded or replaced).
- Mean time to recover (MTTR). The mean time to recover (MTTR) identifies the average (the arithmetic mean) time it takes to restore a failed system (i.e. the downtime)
- NOTE: According to CompTIA, an APT (advanced persistent threat) is a group that has both the capability and intent to launch sophisticated and targeted attacks
- Vulnerability Assessment - The overall goal of a vulnerability assessment is to assess the security posture of systems and networks. They often include the following high-level steps:
- Identify assets and capabilities
- Prioritize assets based on value
- Identify vulnerabilities and prioritize them
- Recommend controls to mitigate serious vulnerabilities
- Vulnerability Scans - A key part of a vulnerability assessment is a vulnerability scan. Security administrators use vulnerability scanners as a management control to identify which systems are susceptible to attacks. An important point about a vulnerability scan is that it does NOT attempt to exploit any vulnerabilities. Instead, a vulnerability scan is a passive attempt to identify weaknesses.
- Penetration Testing - In contrast, a penetration test is an Active test that attempts to take it a step further than Vulnerability Scans do, by trying to exploit vulnerabilities.
- Vulnerability scans are non-intrusive and less invasive than penetration tests. Penetration tests are intrusive and more invasive than vulnerability scans.
- A vulnerability scanner is passive and non-intrusive and has little impact on a system during a test. In contrast, a penetration test is active and intrusive, and can potentially compromise a system.
- False Positive = raising alerts on harmless events (e.g. legitimate email is quarantined or put in spam bucket)
- False Negative = when a real threat is occurring and it’s not detected
- When using Protocol Analyzer (i.e. Wireshark) set the NIC to Promiscuous mode to capture all traffic!
Ch 9 - Business Continuity
- Increasing Reliability == an increase in Availability
- You can add redundancies at multiple levels:
- Disk redundancies using RAID
- Server redundancies by adding failover clusters
- Power redundancies by adding generators or a UPS
- Site redundancies by adding hot, cold, or warm sites
- RAID-0 - Does NOT provide any redundancy or fault tolerance. The benefit of a RAID-0 is increased read and write performance. Because a file is spread across multiple physical disks (req. 2 or > drives)
- RAID-1 - RAID-1 (mirroring) uses two disks. Data written to one disk is also written to the other disk. If one of the disks fails, the other disk still has all the data, so the system can continue to operate without any data loss.
- RAID-2, RAID 3, and RAID-4 are rarely used.
- RAID-5 - has 3 disks and can sustain losing 1 of them only. Offers increased performance and fault tolerance (single drive failure does not destroy the array and lost data can be re-created from the remaining drives).
- RAID-6 - has 4 disks and can sustain losing 2 of them
- RAID-1, 5 and 6 provide fault tolerance
- Hardware RAID is better (performance) than Software RAID, where the disks are managed by the OS
- Failover Clusters - 2 or more servers/nodes (Active/Inactive) with Heartbeat between, to ensure Hi Availability
- Load Balance Clusters - (Hardware or Software) optimize & distribute data loads across multiple computers or networks. Provide Scalability and Availability
- Failover Clusters are appropriate for systems that must share the same data storage. However, Load-Balance Clusters are better when the systems don’t need to share the same storage, cuz load-balancing solutions are less expensive.
- Backup types:
- Full backup. A full (or normal backup) backs up all the selected data
- Differential backup: backs up all the data that has changed or is different since the last full backup
- Incremental backup: backs up all the data that has changed since the last full or incremental backup
- Reasons for choosing backup strategy:
- Full: If you have unlimited time and money, the full backup alone provides the fastest recovery time.
- Full/ Incremental strategies: reduce the amount of time needed to perform backups.
- Full/Differential strategies: reduce the amount of time needed to restore backups.
- Protecting backups includes:
- Storage. This includes using clear labeling to identify the data and physical security protection to prevent others from easily accessing it while it’s stored.
- Transfer. Data should be protected any time it is transferred from one location to another. This is especially true when transferring a copy of the backup to a separate geographical location.
- Destruction. When the backups are no longer needed, they should be destroyed. This can be accomplished by degaussing the media, shredding or burning the media, or scrubbing the media by repeatedly writing varying patterns of 1s and 0s onto the media.
- Steps for BCP (Business Continuity Planning):
- Complete a BIA (Business Impact Analysis) - identify essential critical systems & components that must work. Identify max downtime limits for critical systems.
- Develop recovery strategies.
- Develop recovery plans.
- Test recovery plans.
- Update plans.
- BIA (Bus. Impact Analysis) - is part of a BCP. It documents value of essential (i.e. critical) assets/components/systems including Max downtime & Potential losses. It does NOT include recommendations.
- COOP (Continuity of Operations Planning) - is part of the BCP that provides best practices to mitigate risks and best measures to recover from the impact of an incident. The 3 major COOP steps are to 1) Audit, 2) Mitigate, and 3) Recover
- COOP sites are alternate locations for operations during critical outages. There are:
- hot (active within 60 mins), cold (active within days), warm (60 mins < active < days) and mobile (don’t want fixed location) COOPs.
- DRP (Disaster Recovery Plan) is a part of an overall BCP (Bus. Continuity Plan)
- DRP Phases - Activate Plan / Implement Contingencies / Recover Critical Sys’s / Test Recovery / Document
- Succession Plan - who takes over specific roles/decisions in case of missing resources/personnel
- Testing the Plan:
- Tabletop Exercise - (part of the DRP) is discussion based. A.k.a. “Structured walkthrough”
- Functional Exercise - test plan in simulated operation environment
- IT Contingency plan - part of BCP. Works on a smaller scale than DRP and examines single systems only.
- RTO (Recovery Time Objective) - Max time needed to restore a system to normal state (Max Downtime)
- RPO (Recovery Point Objective) - Point in time where data loss is acceptable (i.e. more than 1 month old). It is the measurement of Accepted Loss by the organization. (i.e. How much data to keep available)
- Alternate Sites: hot (active within 60 mins), cold (active within days), warm (60 mins < active < days)
- Redundant: Duplicate system with seamless failover / Real-time bkups / Doubles costs
- Hot: Datacenter with utilities / all Hard&Soft-ware preconfig’d /
- Warm:
- Cold:
- Fire Categories:
- Class A— Ordinary combustibles. These include wood, paper, cloth, rubber, trash, and plastics.
- Class B— Flammable liquids (e.g. gasoline, propane, solvents, oil, paint, lacquers, synthetics or oil-based products)
- Class C— Electrical equipment. This includes computers, wiring, controls, motors, and appliances. The CompTIA Security + exam is computer-centric, so you should especially understand that a Class C fire is from electrical equipment. You should not fight Class C fires with water or water-based materials, such as foam, because the water is conductive and can pose significant risks to personnel.
- Class D— Combustible metals. This includes metals such as magnesium, lithium, titanium, and sodium.
- Cable Shielding prevents interference (EMI and RFI) and helps prevent attackers capturing traffic
- Hot & Cold Aisles: setup the servers front to front and back to back to avoid pulling heat from one to another. Hot (rising) air is pulled out via air-intake vents in ceiling & cold air is pushed in cold aisles thru vents.
Ch 10 - Cryptography
- Providing Integrity:
- Hashing: MD5, SHA, RIPEMD,LANMAN NTLM
- MD5 - 128 bit hashes
- SHA has four families:
- SHA-0: Not used
- SHA-1: 160 bit hashes
- SHA-2: has four versions: the value indicates the number of bits in the hash
- SHA-224, SHA-256, SHA-384, SHA-512
- SHA-3: different algorithm than SHA-2; produces same size hashes(224, 256, 384, 512)
- HMAC - uses HMAC-MD5 and HMAC-SHA1. First generates a hash using MD5 or SHA1 (providing integrity), then uses a shared secret key to perform another calculation on the hash (providing authenticity). NOTE: IPSec and TLS often use one of the HMAC variations.
- NOTE: Salting passwords with extra characters before hashing adds more security
- RIPEMD - creates hashes of 128, 160, 256, 320 bits
- Older Microsoft hash algorithms used for passwords:
- LANMAN - Win 95/98/ME. Very weak due to padding with spaces. LophtCrack breaks it!
- NTLM - NT Lan Manager is an improvement over LANMAN. Username sent plaintext, but password encrypted.
- NTLMv1: BROKEN! uses MD4 hash and LANMAN for backward compatibility
- NTLMv2: uses MD5. More complex than NTLMv1
- Digital Signatures: are a Hash of a message that is encrypted with the Sender’s Private key, providing Authentication, Non-Repudation, and Integrity
- Providing Confidentiality:
- Symmetric - uses shared (same) secret/session key
- Block Cipher - more efficient for data of known sizes (i.e. files, DB fields, etc.)
- Stream Cipher - more efficient for unknown files sizes & streaming data (e.g. streamed video). IMPORTANT: DO NOT RE-USE KEYS for Stream ciphers!!!
- NOTE: Know the Block and Key sizes listed in the chart below!!!!!!!
- AES - 128, 192 and 256 bits. It is Fast / Efficient / Strong encryption!
- DES - BROKEN via Brute Force. 64 Bit blocks; Small 56 bit keys!
- 3DES - used when legacy hardware doesn’t support AES. 64 bit blocks. Uses 56, 112, and 168 bit keys. More resource intensive than AES
- RC4 - has been used for years in SSL/TLS but rumours are that NSA may be able to break it. Recommendation is to use AES instead now.
- Blowfish - good cipher by Bruce Schneier as DES replacement. Still used today. Uses key sizes between 32 to 448 bits. Encrypts block of 64 bits. Often faster than AES
- Twofish - uses 128, 192, & 256 bit keys. Encrypts data in 128 bit blocks. Was an AES finalist
- OTP (One Time Pad) -Ex. Fob/Tokens. The keys must be TRULY Random, and the key must be at least the same length as the plaintext message. Users must destroy the key after using it once and never reuse a key. Additionally, there should only be two copies of a one-time pad.
- Asymmetric - uses matched pair (public & private) of keys. Very resource intensive encryption & decryption mechanism. Several asymmetric methods require a Certificate & PKI (Public Key Infrastructure). Often only used to exchange keys or passwords (e.g. Symmetric keys).
- Asymmetric Key Types:
- Static - used for long periods of time (i.e. years). These can be validated by CA’s
- Ephemeral - very short life span (often new one is recreated for each session). This type complies with “Perfect Forward Secrecy”
- Diffie-Hellman - a secure key exchange algorithm to privately share a symmetric key b/w two parties. DH methods support both Static and Ephemeral keys:
- RSA uses DH with Static keys
- DHE - Diffie Hellman Ephemeral uses ephemeral keys
- ECDH - Elliptic Curve Diffie Hellman uses Static keys
- ECDHE - Elliptic Curve Diffie Hellman Ephemeral uses ephemeral keys
- RSA - uses math concept of Prime Numbers to generate secure Public/Private key pairs.
- Uses Diffie Hellman with Static Keys
- Min key size = 1024 bits
- Also 2048 and 4096 bit keys are available
- Elliptic Curve Cryptography - ECC often used with small wireless devices (needs little power)
- Steganography - hides data inside other data, but it does NOT actually encrypt the data
- Bit Manipulation - change least-significant bit in some bytes
- White Space - hide data in white space areas
- Steganalysis Detection - Hashing used to compare hash values of files vs baselines
- Quantum Cryptography - uses photons (smallest measure of light)
- S/MIME - Secure/ Multipurpose Internet Mail Extensions is a popular email encryption standard used to digitally Sign & Encrypt email messages.
- PGP/GPG - same as S/MIME
- SSL/TLS - provide certificate based AuthN and use both Asymmetric & Symmetric encryption
- Bcrypt & PBKDF2 - 2 common key-stretching techniques that add salts to passwords as prevention to brute-force and rainbow attacks
- 2 types of Key Exchange:
- In-Band Key Exchange - indicates that the two parties share an encryption key in the same communication channel as the encrypted data. This can be risky because anyone who captures the exchange will have the key and can decrypt the data.
- Out-Of-Band Key Exchange - indicates that the two parties share the symmetric key in one communication channel and then exchange the encrypted data in a separate communication channel.
- Primary purpose of Asymmetric encryption - is to privately share a session key used for symmetric encryption. Another way of saying this is that “asymmetric encryption methods share the session key using an out-of-band key exchange method”.
- PKI (Public Key Infrastructure) - A primary benefit of a PKI is that it allows two people or entities to communicate securely without knowing each other previously. In other words, it allows them to communicate securely through an insecure public medium such as the Internet.
- CA (Certificate Authority) - a key element in PKI
- RA (Registration Authority) - responsible for verifying a user’s identity
- Recovery Agent - has necessary credentials to retrieve files encrypted by another user
- To provide the most secure environment possible for the root CA, companies will often set up the root CA, and then take it offline and allow only child CAs to issue and store certificates.
- OCSP (Online Certificate Status Protocol) - internet protocol for obtaining revocation status of an X.509 digital certificate
- Key Escrow: M of N Control is the key escrow scheme that prevents a single authorized agent from recovering a key. M of N is a mathematical control where N is the number of key recovery agents and M is the number of agents required to perform a recovery.
Ch 11 - Operational Security
- Create Policies ⇒ then create Guidelines & Procedures to support them
- Policies - brief, high-level stmts of org. Goals based on principles/beliefs/mission
- Written Security Policies - are Management Controls that identify a security plan. Other controls enforce them
- Personnel Policies:
- AUP (Acceptable Use Policy) - define/clarify personnel related issues
- Mandatory Vacation policy - helps prevent embezzlement/fraud
- Separation of Duties policy - prevent a single person from completing all functions of processes
- Job Rotation - ensures more oversight. Works well with Separation of Duties
- Account Management Policies:
- Least Privilege Policy: have only rights/access needed for the job
- Account Disablement: disable unused accounts
- NDA (Non-Disclosure Agreements) - ensure 3rd parties understand their responsibilities
- ISA (Interconnection Security Agreement) - specifies Technical & Security reqmts Re: connections. Because they focus heavily on security, ISAs are often written to be legally binding.
- SLA (Svc Level Agreement) - between company & vendor stating performance & svcs expectations
- MOU (Memorandum Of Understanding) - similar to SLA (defines responsibilities) but less formal (i.e. No monetary penalties specified, and no strict guidelines to protect sensitive data). Not legally binding. Often used with ISA
- BPA (Bus. Partner Agreement) - details relationship b/w bus. Partners (obligations, profit shares, etc.). BPAs should describe exactly what the partners are willing to share with each other, and how any inter-organizational access will be handled.
- Change Mgmt - reduce risk related to unintended outages & provide documentation of all changes
- Data Policies:
- Data Privacy Policy - specifies how web sites use/disclose visitor info
- Social Media Policies - warn against divulging info (reduce Cognitive Password Attacks) and also reduced activity helps to avoid Banner Ad & Malvertisement attacks
- Incident Response:
- First step = Create Incident Response Policy (see NIST SP 800-61 Rev 2)
- Chain of Custody - provides assurance that evidence has been controlled/handled properly
- Order of Volatility: collect evidence starting with most volatile to least…
- Cache memory & Registers data (including processor cache & hard drive cache)
- RAM memory data (including system & network processes), routing table, ARP cache, process table, and kernel statistics
- Temporary file systems, such as Swap file or paging file on the system disk drive
- Data stored on local disk drives
- Physical configuration, network topology
- Logs stored on remote systems
- Archive media